Advances in the fight against malware have taken a significant turn with the introduction of innovative techniques based on machine learning. Researchers have developed numerous malware detection methods utilizing these technologies; but as detection methods improve, so too do the techniques employed by malware creators. The back-and-forth between malware development and detection systems has opened the door to challenges, particularly as malicious software continues to evolve.
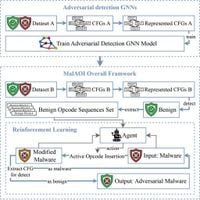
A recent study published on March 18, 2025, highlights such advancements with the introduction of the active opcode insertion technique, which is specially engineered to modify portable executable (PE) malware control flow graphs (CFGs). This novel modification strategy not only allows for functionality retention but also enables the generated malware to survive detection by graph neural network (GNN) models, which are increasingly being leveraged for malware identification.
The key to this new approach lies in reinforcement learning (RL), which is employed by the novel system called MalAOI. This system works by identifying optimal insertion points for benign opcode sequences, ensuring the modified malware maintains its functionality all the time. The researchers conducted extensive tests on datasets, namely BODMAS and SOREL-20M, to fine-tune and validate their methods.
According to the authors of the article, "MalAOI-generated adversarial malware achieves an average evasion rate of 93.73% against the GNN detection model." Remarkably, the study noted only a 12.87% increase in file size after malware was modified using their approach, indicating its efficiency and viability.
The BODMAS dataset used for testing MalAOI contained approximately 57,293 malware samples alongside 77,142 benign samples. This data, collected between August 2019 and September 2020, helped underline the significance of this work against the backdrop of growing malware threats.
A startling finding from the analysis also revealed the average 'malicious probability' of the original malware stood at 80.15%, whereas the generated adversarial samples showed only 59.77%. This translates to an overall reduction of 20.38% across the board, showcasing the effectiveness of MalAOI to evade detection.
This sleek and effective method isn't just providing solutions for researchers; it raises pressing questions about the capabilities of traditional malware detection mechanisms. While GNN-based models have proven to be effective, this research calls attention to the new challenges systems face as malware systems become increasingly sophisticated.
Digging deep, the methodology of active opcode insertion highlights the systematic approach employed by researchers. By ensuring functional - or operationally preserving - attacks against GNN models, MalAOI modifies the underlying CFGs through strategic positioning and benign opcodes. This step is propelling malware evolution amid defenders employing more stringent and advanced security measures.
The experimental results are quite illuminating: MalAOI exhibited strong attack success rates against various GNN-based models, demonstrating its capacity to function effectively regardless of model complexity or structure. Not only does the mechanism serve its purpose against the datasets used, but it also indicates transferability across different forms of GNN architectures, with efficacy remaining comparatively high.
The segment of research dedicated to malware prevention is of primary importance to safeguarding digital infrastructures worldwide. MalAOI demonstrates high adaptability, making it useful for actors intending to modify GNN detection capacity based on CFGs. Meanwhile, it simultaneously reveals the vulnerabilities within existing detection systems.
Concluding on this groundbreaking line of inquiry, the authors express optimism for future developments, stating, "This study encourages researchers to improve their detection models and conduct adversarial training to mitigate threats associated with increasingly complex malware challenges." More comprehensive research will be necessary to fortify defenses and explore the broader ramifications for cybersecurity strategy, ensuring security protocols evolve as threats develop.