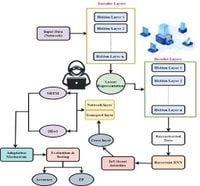
In an era where the Internet of Things (IoT) continues to expand, the need for robust security measures against cyber threats has never been more critical. Researchers have introduced a groundbreaking approach via the Multi-Layer Deep Autoencoder (M-LDAE), specifically tailored for cross-layer IoT attack detection. This innovative framework combines the power of advanced deep learning algorithms to enhance threat detection capabilities, adapt to emerging methods of attack, and address the complex nature of IoT networks.
The M-LDAE framework stands out in its ability to identify intricate assault patterns that may span multiple protocol layers, ensuring comprehensive protection across various IoT ecosystems. Utilizing deep learning techniques such as Recurrent Neural Networks (RNNs), Graph Neural Networks (GNNs), and Temporal Convolutional Networks (TCNs), the M-LDAE is equipped to tackle the sophisticated challenges posed by modern cyber threats.
Simulation results demonstrate that M-LDAE enhances detection accuracy while significantly reducing false positives. In extensive tests involving 1,379,274 total data flows—of which 1,108,995 (80.4%) were identified as attack samples and 270,279 (19.6%) were benign—the M-LDAE achieved an impressive accuracy of 94.8%. These findings suggest that this new model not only meets but exceeds performance benchmarks compared to existing detection methods.
One of the critical innovations of the M-LDAE is its approach to anomaly detection through reconstruction error analysis. This technique helps the system accurately identify attacks, including Man-in-the-Middle (MitM) and Distributed Denial of Service (DDoS) attacks, by interpreting the relationships hidden within network data. By employing ensemble learning measures and thresholding methods, the M-LDAE framework further improves reliability and reduces false alarms, demonstrating a low false positive rate of just 6.8%.
The intricate design of the M-LDAE promotes hierarchical learning, allowing it to analyze and adapt to diverse threats seamlessly. Cross-layer integration helps capture network dynamics that are unique to IoT communications, making the system resilient against constantly evolving cyber-attack strategies. As IoT devices proliferate globally, safeguarding these interconnected systems becomes increasingly vital.
Moreover, the M-LDAE not only detects existing threats but is also capable of adapting to new forms of cyberattacks. During testing, it experienced a 7–10% accuracy drop under adversarial attack simulations, yet innovative adversarial training recovered some accuracy while slowing false positive rates. This indicates the model’s robustness and potential for continued learning and adjustment in real-world scenarios.
In real-time applications, the significance of rapid threat detection and mitigation cannot be overstated. M-LDAE’s ability to monitor and respond to threats at various layers of network protocols is imperative for maintaining the integrity of IoT infrastructures. Its detection mechanism allows for immediate reactions to suspicious activities, greatly enhancing the overall security posture of connected devices.
This achievement is the outcome of intensive research and development efforts focused on leveraging advanced deep learning algorithms to build a refined intrusion detection system capable of meticulous cybersecurity. Researchers believe that the introduction of the M-LDAE can represent a paradigm shift in how we approach IoT security.
In conclusion, as IoT ecosystems become more intricate, the challenges associated with securing them will continue to grow. The M-LDAE offers a promising solution, paving the way for greater resilience against multifaceted cyber threats. Future research should focus on optimizing the usage of the M-LDAE for various real-world applications while continuously improving its detection capabilities. This approach could onclude critical advancements across different domains, including smart agriculture, healthcare, and urban management, thereby significantly enhancing IoT security protocols worldwide.