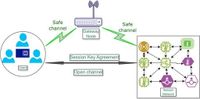
The integration of the Internet of Things (IoT) with Wireless Sensor Networks (WSNs) has heralded a new era of intelligent systems that can monitor and manage various environments, including smart cities and healthcare systems. However, as these networks expand, ensuring robust security measures becomes paramount, particularly for protecting sensitive data transmitted across potentially vulnerable channels. A novel two-factor authentication (2FA) protocol proposed by researchers addresses these security challenges by leveraging the power of Elliptic Curve Cryptography (ECC) and a fuzzy verifier, effectively enhancing the safety of IoT-enabled WSNs while maintaining efficiency.
This innovative approach emerges from the recognition that traditional authentication methods often fall short, particularly in environments where resources are limited. The introduced 2FA method not only strengthens security but also confronts the longstanding security-usability conflict by minimizing the processing requirements associated with complex authentication protocols. "The computational cost of our proposed scheme is 8.9569 ms, significantly lower than existing models," stated the authors of the article, illustrating the practical benefits inherent in their design.
In developing their protocol, the authors applied a fuzzy verifier concept, which introduces randomness into password verification. Instead of relying solely on deterministic hashing of passwords, this technique enables the system to accommodate minor variations during user authentication, thereby enhancing user experience without compromising security. By employing a method that blends the flexibility of fuzzy authentication with the robust security framework of ECC, the researchers effectively tackle common attacks associated with IoT security vulnerabilities, such as offline password guessing and identity theft.
The methodology describes a system that operates through a Gateway Node (GWN), which acts as a trusted intermediary between users and sensor nodes. The GWN executes a five-part procedure involving initialization, registration, login, authentication, and password management, securely supporting the interactions of all components in the network. Each user and sensor node undergoes registration with the GWN, which generates unique security parameters that are crucial throughout the authentication process. This design helps to mitigate the risks posed by man-in-the-middle attacks and unauthorized access.
In terms of performance metrics, the communication cost of the proposed protocol totals 2496 bits, demonstrating a notable reduction when compared to existing authentication schemes. This efficiency is pivotal since excessive communication overhead can stagger system responsiveness and resource allocation in constrained environments. With the alternating emphasis on security and usability, the authors highlight that their method allows for practical implementation in real-world applications where limited resources are often a constraint.
The findings of this research hold considerable implications for the future of IoT applications, particularly as the technology continues to evolve and expand into new areas. As the authors suggest, additional improvements could ultimately lead to more adaptive authentication strategies, possibly incorporating machine learning to enhance usability while further fortifying security protocols in dynamic environments.
Overall, the proposed 2FA technique represents a significant step forward in the quest to secure IoT-enabled WSNs, merging advanced cryptographic methods with flexible user verification processes. Future work will aim to refine the versatility of this approach, potentially enabling its application across various sectors reliant on secure, streamlined data transmission and integrity.