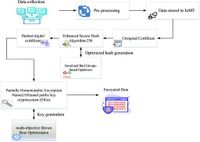
The rapid expansion of the Internet of Medical Things (IoMT) has transformed the healthcare industry, allowing for real-time monitoring and seamless data exchange between medical devices. However, as these technologies become more integrated into daily healthcare practices, concerns over data privacy and security intensify. A new security framework, known as ESHA-256_GBGO, combines advanced encryption techniques to safeguard sensitive medical data against potential cyber threats, promising enhanced security and efficiency in IoMT applications.
The ESHA-256_GBGO framework merges the Enhanced Secure Hash Algorithm-256 (ESHA-256) with the Golden Butterfly Optimization (GBGO) algorithm to optimize data encryption processes. This innovative approach aims to tackle the security shortcomings of existing models, which often face high computational costs and inefficiencies in managing large-scale IoMT data. As cyberattacks become more sophisticated, there is an urgent need for robust encryption that can operate effectively in real-time healthcare settings.
The researchers behind the ESHA-256_GBGO framework have found that traditional encryption methods, such as the Advanced Encryption Standard (AES) and Rivest-Shamir-Adleman (RSA), often result in delays and excessive energy consumption when implemented on resource-constrained IoMT devices. The ESHA-256 algorithm offers a lightweight alternative that maintains strong data integrity without incurring heavy computational overhead. Furthermore, the GBGO algorithm precisely optimizes encryption parameters to improve overall efficiency, helping reduce latency during critical healthcare responses.
In evaluating the effectiveness of the ESHA-256_GBGO framework, the researchers implemented it on a real-world IoMT dataset focused on healthcare monitoring. They measured key performance indicators such as encryption efficiency, processing time, throughput, and computational overhead. Results demonstrated that the proposed model achieved a remarkable 98.76% encryption efficiency while simultaneously reducing computational overhead by 27.4%. These findings suggest that the framework not only enhances security robustness but also ensures quick, real-time data processing vital for healthcare applications.
The integration of advanced hashing techniques, optimization strategies, and adaptive security policies positions the ESHA-256_GBGO model as a comprehensive solution for the unique data protection challenges posed by IoMT environments. This approach provides scalability and efficiency, ensuring that sensitive medical data remains secure while allowing healthcare providers to focus on patient care.
This research emphasizes the critical need for developing optimized security frameworks that adapt to the evolving landscape of cyber threats in IoMT. The successful implementation and testing of ESHA-256_GBGO represent a significant step toward achieving better security practices across healthcare data systems. The study concludes that with this framework, healthcare providers can confidently utilize IoMT technologies while ensuring their patients' data remains protected from unauthorized access.
In conclusion, the ESHA-256_GBGO security framework signifies a major advancement in the field of IoMT security, effectively addressing the pressing issues of data integrity and confidentiality. Future developments may integrate even more adaptive components, such as blockchain technologies and edge computing solutions, to enhance real-time security features and provide a stronger defense against emerging cyber threats.